Topic: Cybersecurity
Responsibilities: Training Needs Assessment, Instructional Design, e-Learning Development, Implementation
Target Audience: Global Employees
Tools Used: Articulate 360 Storyline
Year: 2018, 2019
Instructional Design Process:
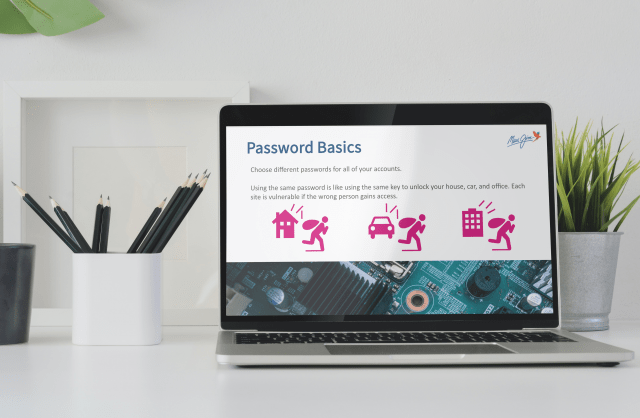
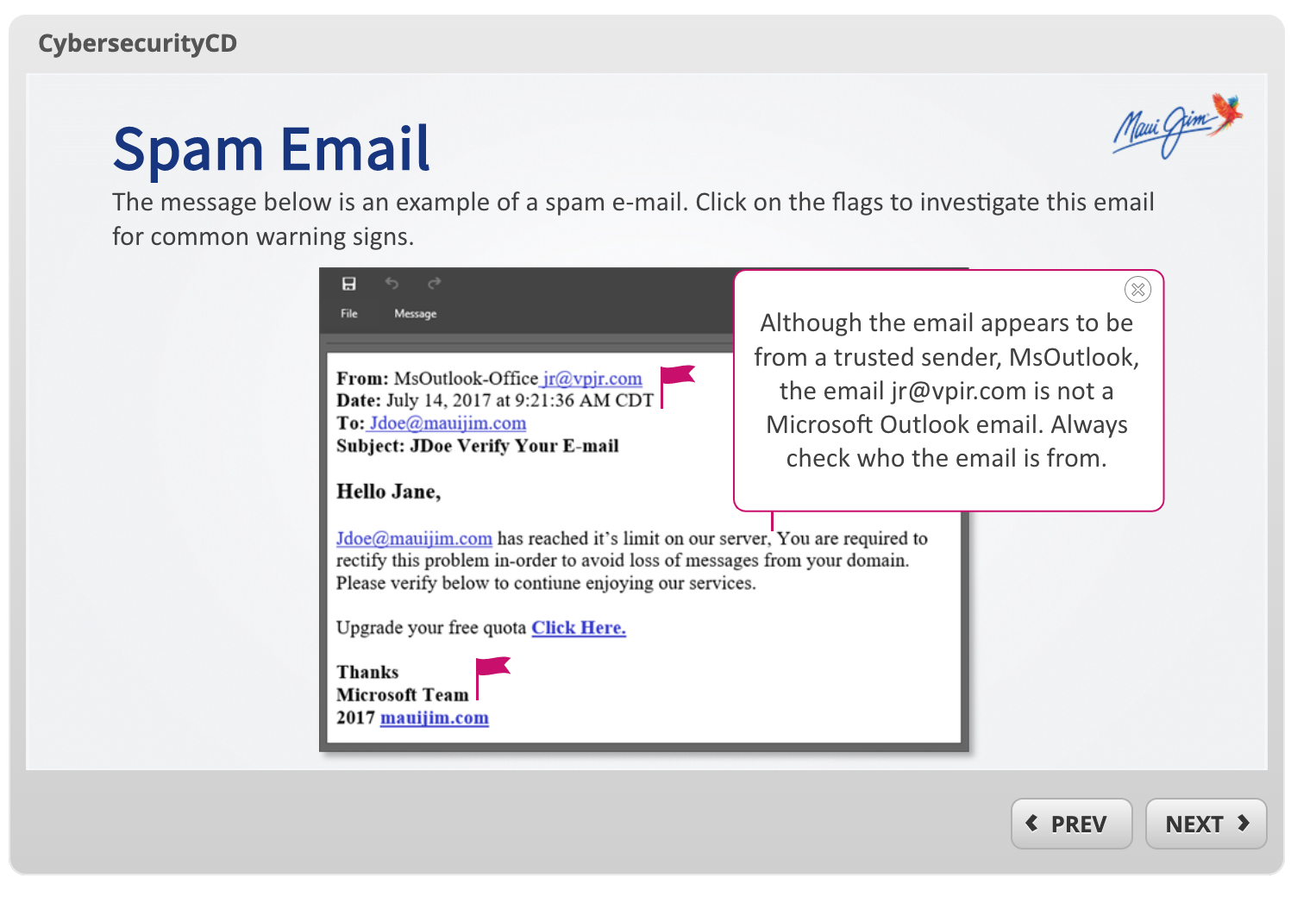
The director of IT reached out to the training team to see what was available for company-wide cybersecurity compliance training. He specified that we need to educate our users on how to safely use their machines with the goal of decreasing the number of interactions with spam emails. After reviewing pre-made content available on a third-party site, it was determined that the external content was not going to match the culture and compliance needs of the company.
Since this would be the first e-learning and the first compliance training pushed out to the entire company, I wanted to be sure that the e-learning was simple to follow and offered activities to reinforce what the user learned. I started the process by reviewing the cybersecurity policy and researched what the industry standards were for cybersecurity compliance training. I then drafted an outline of content, learning objectives and storyboard for the director of IT to review.
eLearning Development:
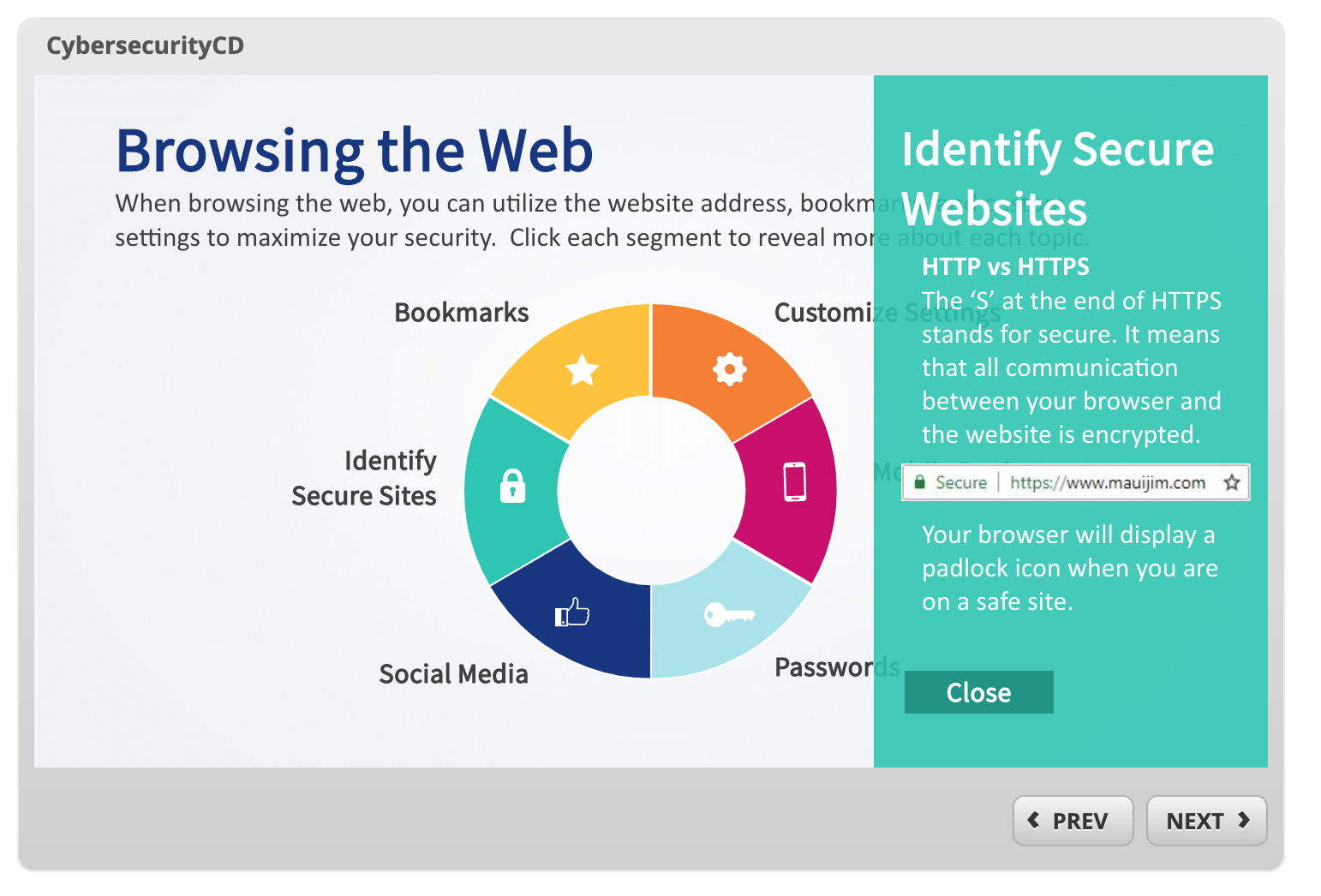
With approval on the content and flow, I started building the content in Articulate 360 Storyline. The course was designed with mobile needs in mind. I was sure to keep text and objects large enough to read and interact with on a mobile device. I incorporated activities and interactions where appropriate in the flow of content. The design of the eLearning was linear. The learner would follow the content and complete the activities in order to advance the training. A short quiz was added to the of the eLearning to act as a knowledge check and satisfy level 3 of Bloom’s taxonomy.
Implementation:
After finalizing the project and exporting as SCORM, I uploaded the e-learning course to the Cornerstone LMS, created a deep link for the course, and drafted an email for the IT Director to send out.
I then tracked completions and reached out to individuals and managers to encourage accountability for completing the training. Since this was an annual training, I later reviewed the project and reached out to the IT director to see if there was anything to add to the new version of the training. With his additions, I was able to update the training, assign it out, and track completions to ensure the company is in compliance.
Outcome:
The e-learning satisfied the compliance training need while also feeling authentic to the companies culture. Employees were thankful for a great resource and felt that they had the tools they needed to safely use their computers. A few months after the launch of the training, the IT director sent out a fake spam email to test our employees. He was pleasantly surprised to see that interactions with spam emails decreased substantially and the reporting of spam messages increased. This test proved that the cybersecurity microlearning provided users with knowledge and tools for application. The success with this project led to many future projects with IT including PCI and GDPR trainings.